
ADDISON, Texas, February 10, 2021 – Authentix®, the authority in authentication and information services, announced it will be sponsoring International Petroleum (IP) Week February 23-25, 2021, hosted by the Energy Institute. The event, held virtually this year, remains the preeminent international event for building collaboration between the oil and gas industry, government, and society.
Virtual IP Week 2021 will focus on the urgency and demand for the industry to move to a lower carbon future over the next decade, with executives and leaders across the globe collaborating to help define the industry’s role and actions towards this critical endeavor.
Jeff Conroy, PhD, Chief Technology Officer for Authentix, will be presenting February 24th on the topic of “Innovative Solutions for Quality Assurance and Source Integrity of Renewable Biofuels”. With expectations to reduce reliance on crude oil derived hydrocarbons and move to cleaner, renewable, lower carbon alternatives, oil companies are looking at ‘second generation’ or ‘advanced biofuels’ to fill that need.
Already in Europe there is a mandate for the use of these biofuels derived from waste (as outlined in RED and REDII) and allowing for double counting of these in meeting the targets required. This adoption of a wider range of biofuels obtained from a larger variety of sources has increased the complexity in the supply chain, which in turn increases the need for greater oversight and control by both oil companies and governments. In Conroy’s presentation, IP Week delegates will learn how the new QualiTrax™ rapid fuel quality testing solution, a cutting-edge digital field-based fuel quality system using machine learning, artificial intelligence, and real-time access to data can help verify the proper sources and supply integrity for new biofuels.
As part of its sponsorship, Authentix will also have a digital exhibit booth for delegates to explore and chat with an executive to learn more about the QualiTrax fuel quality solution and other fuel integrity programs.
To register for IP Week or for more information, visit the event website at www.ipweek.co.uk.
About Authentix
As the authority in authentication solutions, Authentix thrives in supply chain complexity. Authentix provides advanced authentication solutions for governments, central banks and commercial companies, ensuring local economies grow, banknote security remains intact and commercial products have robust market opportunities. The Authentix partnership approach and proven sector expertise inspires proactive innovation, helping customers mitigate risks to promote revenue growth and gain competitive advantage. Headquartered in Addison, Texas USA, Authentix, Inc. has offices in North America, Europe, Middle East, and Africa serving clients worldwide. Authentix® is a registered trademark of Authentix, Inc. For more information, visit www.authentix.com.
About The Energy Institute
The Energy Institute is the not-for-profit chartered professional membership body bringing together expertise to tackle urgent global challenges. Responding to the climate emergency while meeting the energy needs of the world’s growing population calls for energy to be better understood, managed and valued. This ambition is at the heart of our social purpose. We are a global, independent network of professionals spanning the world of energy, convening and facilitating debate, championing evidence and sharing fresh ideas, giving voice to issues of concern and where necessary challenging the industry we work with. For more information, visit https://www.energyinst.org.


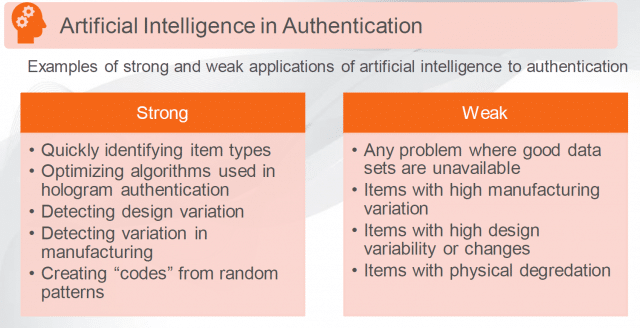
 The current counterfeit landscape is a “not if, but when” environment. At some point, brand owners will experience an unauthorized product in their supply chain. Given this inevitability, your product security strategy should be thorough, with a strong emphasis on implementation planning to enable detection of problems and action to mitigate and manage accordingly. One of the most effective deterrents to risk is teaming with a partner with the requisite skills, experience and talent to assist you in all facets of brand protection.
The current counterfeit landscape is a “not if, but when” environment. At some point, brand owners will experience an unauthorized product in their supply chain. Given this inevitability, your product security strategy should be thorough, with a strong emphasis on implementation planning to enable detection of problems and action to mitigate and manage accordingly. One of the most effective deterrents to risk is teaming with a partner with the requisite skills, experience and talent to assist you in all facets of brand protection. In articles
In articles  ADDISON, Texas, July 23, 2020 – Authentix, the authority in authentication solutions, welcomes David B. Brown to the executive team in the role of Chief Financial Officer. Mr. Brown will be responsible for integrating business and finance strategy to further expand the global presence of Authentix and drive growth into key markets. In his role, Mr. Brown brings over thirty years of experience as he oversees global finance, treasury, accounting and taxation activities.
ADDISON, Texas, July 23, 2020 – Authentix, the authority in authentication solutions, welcomes David B. Brown to the executive team in the role of Chief Financial Officer. Mr. Brown will be responsible for integrating business and finance strategy to further expand the global presence of Authentix and drive growth into key markets. In his role, Mr. Brown brings over thirty years of experience as he oversees global finance, treasury, accounting and taxation activities. ADDISON, Texas, July 20, 2020 – Authentix®, the authority in authentication and information services, announced that its Senior Vice President and General Manager of Tax Stamp & Currency, Tim Driscoll, Ph.D., will be presenting an industry webinar titled Quarantining Illicit Tobacco – Tobacco Control through the Lens of COVID-19 on July 23, 2020, at 9:00 AM Central Standard Time.
ADDISON, Texas, July 20, 2020 – Authentix®, the authority in authentication and information services, announced that its Senior Vice President and General Manager of Tax Stamp & Currency, Tim Driscoll, Ph.D., will be presenting an industry webinar titled Quarantining Illicit Tobacco – Tobacco Control through the Lens of COVID-19 on July 23, 2020, at 9:00 AM Central Standard Time.
 ADDISON, Texas, July 15, 2020 – Authentix®, the authority in authentication solutions, shares positive results of continued client partnerships for Corporate Social Responsibility (CSR) initiatives. Through a long standing commitment to expand resources beyond standard business operations, Authentix has taken lead from its government partners to help deliver a lasting, positive impact on the lives of thousands in many communities in Africa.
ADDISON, Texas, July 15, 2020 – Authentix®, the authority in authentication solutions, shares positive results of continued client partnerships for Corporate Social Responsibility (CSR) initiatives. Through a long standing commitment to expand resources beyond standard business operations, Authentix has taken lead from its government partners to help deliver a lasting, positive impact on the lives of thousands in many communities in Africa. Ghana: New Technology Laboratory in Kongo Senior Secondary School
Ghana: New Technology Laboratory in Kongo Senior Secondary School
 Covert or Semi-Covert Security Features – Covert and semi-covert features are invisible to the naked eye or disguised but can be found and measured with specialized handheld devices using proprietary optics and detection algorithms for rapid, secure field authentication.
Covert or Semi-Covert Security Features – Covert and semi-covert features are invisible to the naked eye or disguised but can be found and measured with specialized handheld devices using proprietary optics and detection algorithms for rapid, secure field authentication. One Tactic Is Not Enough
One Tactic Is Not Enough