Table of Contents
- What Is Brand Protection and Why is it Necessary?
- Forms of Brand Protection Solutions and Providers
- The Global Impact of Illicit Trade and the Purpose of this Guide
- How Infringement/Counterfeiting Harms Brands and Their Customers
- Types of Brand Infringement and Counterfeiting
- Steps for Developing and Implementing a Brand Protection Strategy
- What Brand Protection Solutions Are Right for My Company?
- Implementing a Multilayered Approach: How Brand Protection Works
- The Future of Brand Protection
- Benefits of Having a Brand Protection Partner
- What to Look for in a Brand Protection Partner
- About Authentix Brand Protection Solutions
What Is Brand Protection and Why is it Necessary?
Counterfeiting, smuggling, diversion, and infringement — collectively known as illicit trade, — continues to be a growing global problem for businesses and consumers. With the increasing volume of counterfeit goods trafficked across the globe and seeping into multiple supply chains, a well-strategized brand protection program is more essential than ever to shield what matters most to businesses – customers, brand identity, reputation, and revenue.
This growing illicit trade epidemic extends across a multitude of industries — food and beverage, pharmaceutical, health and beauty, apparel, and a host of other consumer and commercial products. The effects translate into financial losses for brand owners, and, more importantly, added risks to consumer health and safety. Falsified products manufactured without regard for standards, required ingredients, quality control, or government oversight, can imperil consumer safety and create a lack of confidence in a trusted brand.
A thoughtfully developed brand protection program benefits brands by protecting their intellectual property, customers, revenue and reputation.
Brand protection encompasses developing strategies and selecting solutions aimed at safeguarding a company’s sizable investments in R&D, testing, marketing, tooling, and quality control to develop a valuable and premium brand of products. This includes protecting investments in trademarks, copyrights, patents, products, and proprietary designs, from unauthorized use. It is critical for companies to defend their brand identity and maintain their reputation against the threats posed by counterfeiters, copycats, and various forms of illicit trade and IP abuse.
Forms of Brand Protection Solutions and Providers
Working with federal and local law enforcement, customs, and border protection agencies can prove to be effective,. However, it is extremely time-consuming and requires close collaboration with said authorities. Most companies and brands applaud criminal convictions of perpetrators. But it is difficult to persuade law enforcement to prioritize counterfeiting over other crimes, and building solid cases to convict bad actors is becoming increasingly difficult.
Therefore, the most effective course of action to protect brands is via prevention by applying physical protection at the point of manufacture and actively monitoring e-commerce platforms. Thus, there are two primary approaches to creating and sustaining the protection of brands across the global supply chain:
Online Brand Protection
Online Brand Protection services involve extensive monitoring of the e-commerce platforms and marketplaces that exist across the world wide web for the detection of fraud, prioritizing the risks noted, and invoking enforcement action against the infringing parties.
This may be accomplished through contracting with a provider possessing special software tools that are designed to scan hundreds of online marketplaces periodically and specifically search for key phrases, keywords, images, and trademarked logos. These tools use algorithms to determine the similarity between the found listings and the brand owners’ trademarks, product descriptions, images, logos, etc.
When similarities are discovered, these specialized software tools can also infer the key differences and anomalies that flag those listings as suspect. However, just detecting potential anomalies between legitimate and potentially illegitimate listings is only the beginning. A provider must also utilize highly sophisticated software and algorithms to analyze each suspect listing and rank it in order of relevance and threat level to prioritize and determine potential remediation and brand protection enforcement action.
There are established protocols among many of the most popular e-commerce marketplaces to allow brand owners or their provider designates to identify and forcibly remove or “take down” fraudulent listings and infringing websites through a standardized set of actions.
Some online brand protection providers offer a DIY solution giving the brand owners access to a software platform. But most of the management of the system and follow-up enforcement requires direct action by the brand owner’s personnel. Depending on the number of brands in the portfolio and the pervasiveness of the product’s appeal globally, this can be a daunting effort by companies not having a large staff devoted to this singular issue.
Other providers utilize a turnkey approach taking direction from only one or a few key stakeholders from the brand owner’s representatives based on daily or weekly findings of risk detection. They then carry out the instructed enforcement actions and follow up with notifications on the brand owner’s behalf. Some full-service providers even offer sample purchase services where products from the suspected listing sites are ordered and received for physical inspection (using standards provided by the brand owner).
Further, a full-service provider has the capability to launch formal investigations and maintain a detailed case management file and reporting system as the investigation is carried out by the provider’s employees, private contractors, and even local authorities having jurisdiction in the case(s).
Physical Supply Chain Protection
Using Online Brand Protection services is a potential key strategy to detect and deter online fraud from being perpetrated against a company. In addition, many companies deploy physical protection for their products using overt (blatantly visible) and covert (hidden) physical security features. These measures allow quick inspection in the distribution chain to detect a potentially falsified or diverted product posing as a legitimate, genuine article.
This is especially true for premium products available through vast retail and merchandise distribution systems, such as medicines, cosmetics, wine and spirits, electronics, auto parts, and many other premium brands found on retailers’ shelves. Physical supply chain protection involves placing either a covert, semi-covert, and/or overt feature on the packaging or label of the product. In some cases, a semi-covert feature is chosen whereby a visible feature on the package or label may require additional manipulation or interaction to make the hidden feature visible.
The Global Impact of Illicit Trade and Purpose of this Brand Protection Guide
Consider this: The total amount of counterfeit goods and overall illicit trade each year is approximately $2.0 trillion, a bit less or more depending on the source referenced. This also accounts for over 2.5 million lost jobs globally. All international and domestic businesses and consumers can be victims of counterfeiting. For example, consumers in the United States tend to purchase the highest value of counterfeit goods at around 60% to 80% of all counterfeit products sold. (Forbes, 2022)
This comprehensive guide examines several matters for brand owners to consider when developing and executing a brand protection program. Our review includes both online brand protection and physical supply chain protection. This brand protection guide addresses:
- Both facets of execution (online and physical)
- Key areas of vulnerability
- Best practices to implement an effective program
- Ways to evaluate the best technology partner
- Some of the more interesting and emerging technologies that are entering the market
How Infringement / Counterfeiting Harms Brands and Their Customers
Infringement and illicit trade can create a web of negative impacts that harm brands and their customers, often jeopardizing the consumer experience when customers unknowingly purchase a product that proves to be falsified. Fake products result in economic harm to businesses through decreased revenue and increased warranty or return claim reimbursements. They also degrade the brand’s reputation, leading to a loss of consumer trust.
The effects stretch beyond financial loss, often posing environmental risks and endangering public health and safety with hazardous products. In addition to the potential risk of harm to consumers, legal and liability issues can arise. Add to the mix potential phishing scams, fake online product listings and social media accounts, etc., and there are many risks for brands and consumers when illicit trade happens.
-
Counterfeits threatening a customer’s health and safety: The impact of counterfeits goes far beyond financial losses; it puts consumer health and safety at risk. Some of the most dangerous counterfeit products include prescription drugs, automotive parts, electronics, and cosmetics or personal care items.
Counterfeit prescriptions lead to serious illness, accidental overdoses, and even death. Counterfeit cosmetic products can cause severe skin reactions due to poor-quality materials and formulation. Counterfeit batteries can cause fires or even explode. Even counterfeit clothing and shoes have been shown to have higher levels of heavy metals than the genuine products would ever allow. The risk that someone could get hurt or killed due to a dangerous fake product exists in practically every industry. - Economic harm: When counterfeiters produce falsified products at a discount price, revenue potential for the brand owner is undoubtedly affected. Customers may also turn to a competitor’s product after experiencing a low-quality counterfeit bearing the premium brand’s name.
- Environmental and social impact: Counterfeits are often produced using hazardous and cheaply sourced, substandard materials that pollute the environment. Illicit manufacturing also takes advantage of exploitative labor, poor working conditions, and unpaid labor to keep costs down. As companies worldwide take steps to invest in sustainability, counterfeits can be an environmental disaster.
- Negative brand perception: A brand works hard to build its reputation and gain consumer trust. It only takes a few bad actors producing counterfeits to tarnish a reputation and lose consumer trust when customers no longer see highly regarded brands as reliable and high-quality.
- Legal exposure and liability in lawsuits: If the need arises to prosecute counterfeit manufacturers, it can be a huge drain on company resources. Legal teams are expensive, and the process can be incredibly slow as it works its way through the court system. It can also be very difficult to recoup legal fees. In some countries and jurisdictions, the penalties for counterfeiting differ greatly and add to the problems pursuing this angle.
- Phishing scams taking advantage of customers: Fraudulent websites that appear to offer genuine products can be phishing scams designed to steal a consumer’s personal information and carry out identity theft.
Types of Brand Infringement and Counterfeiting
Nothing erodes brand trust faster than an unexpected public disclosure of product falsification, recalls, consumer harm, or legal action against a brand. This can prove toxic to any popular brand. These outcomes often result from organized criminal activity in the supply chain. Criminals have a sophisticated network of willing players in practically every industry. Profiteers typically target high-value products with strong consumer demand in especially lucrative industries, such as pharmaceuticals, spirits, health and beauty, and fuel. Knowing how to protect your brand means understanding how these profiteers work.
Here’s a snapshot of some of the tactics used by criminals today:
Physical Supply Chain Compromise:
- Counterfeiting: Products are produced to imitate the genuine offering using subpar or even dangerous ingredients and presented as authentic
- Grey Market Sales: This occurs when genuine products are sold in a specific market or economic area without the permission of the trademark owner. These real products are redirected and sold through unofficial channels without the approval of the person or company that owns the trademark.
- Diversion: Genuine products are smuggled or diverted without manufacturer authorization from lower-priced to higher-priced markets.
Case Study: Fast-Moving Consumer Goods
The Challenge
A large, global hair care manufacturer produces category-leading brands with high consumer loyalty and demand. Their products are high-value targets for counterfeiters, organized theft rings, and gray market wholesalers. In fact, the manufacturer found they were being negatively impacted by the diversion of its products from legitimate distribution channels into gray or retail markets. This situation was creating dissatisfied customers and weakening their promotional efforts.
The Solution
Authentix implemented an authentication solution of serialization and a track and trace system that identified product diversion in the brand’s distribution channels for over 165 million products. The Authentix solution utilized multiple covert authentication features that allow item-level serialization and full product traceability from manufacturing to retail, as well as provisions to track repackaged products.
The Outcome
- Successfully identified channel leaks within a complex distribution chain of over 2,500 channel partners and 15 distributors
- Over 300 million units have been marked since the Authentix solution was implemented
- 47 percent reduction in product diversion
- Consequently, product sales increased by $77 million
Learn more: https://authentix.com/cpg-case-study/
- Tampering: Packaging or containers are refilled or reused with illegitimate ingredients or dosages with intent to deceive the consumer. This includes legitimate products that are expired, re-labeled, and misrepresented.
- Adulteration: For purposes of dilution or volume substitution, some dangerous or low-quality substances are added to genuine products, including food, cosmetics, biologics, fuel, or other chemicals.
- Patent Theft: Patent theft, or patent infringement, occurs when someone makes or sells a patented product without the inventor’s permission, violating the exclusive rights granted by government authorities for new, original inventions or innovative solutions to problems. This infringement can pertain to both the design and utility of a product, focusing on visual aspects in design patents and functional similarities in utility patents.
Online or E-Commerce Compromise:
- Copyright Infringement: Copyright infringement is the unauthorized copying, distribution, or display of protected copyrights including products, designs, written works, videos, photos, and more.
- Trademark Infringement: Trademark infringement involves the unauthorized use of a brand’s trademarks such as words, logos, or designs, leading to consumer deception or confusion. This can occur both intentionally, through the sale of counterfeit goods, and unintentionally when similar marks cause confusion about the product’s source.
- Illicit Website Domains: Rogue or copycat websites are fake sites designed to look like a brand’s official website. Sometimes, the perpetrator might use a web address that’s very similar to a particular brand with minor changes, tricking people into thinking it’s the genuine site. Other fake sites might not try as hard to mimic a brand’s official look, making them easier to recognize as frauds, but they all aim to sell fake versions of products and pretend they’re authentic.
- Social Media Impersonation: Social media impersonation refers to the creation of fake social media accounts that mimic legitimate brands, with the goal of misleading consumers into buying counterfeit goods or visiting phishing websites or exposing them to malware. This form of infringement poses a significant challenge for brand protection, as it exploits brand identity and damages consumer trust.
- NFT Infringement: In the world of Non-Fungible Tokens (NFTs), the creator who first makes the NFT owns the rights to it. If someone else creates an NFT using original content without the brand owner’s permission, it’s essentially theft and violates copyright laws related to NFTs. To keep the brand safe from these types of infringements, it’s important to keep an eye out for any unauthorized use of content on NFT marketplaces around the world.
Steps for Developing and Implementing a Brand Protection Strategy
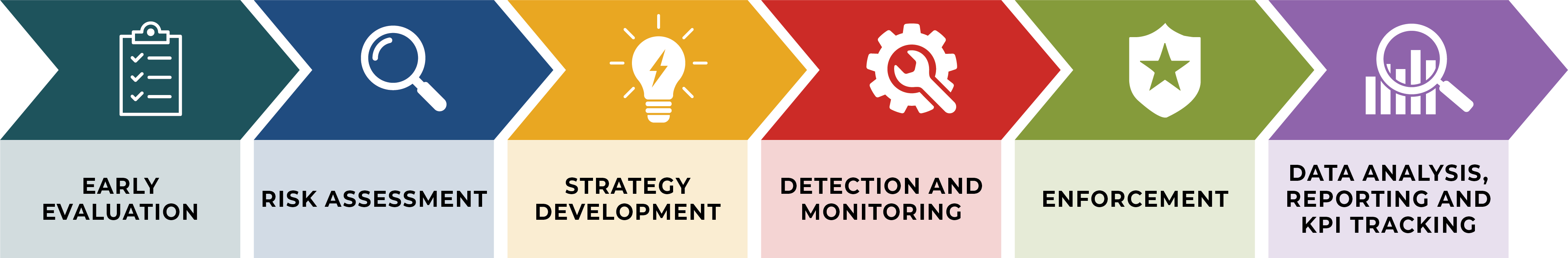
Creating a brand protection plan for companies means working together across different parts of the company and locations around the world. It also means building relationships with outside groups like customs, police, and government agencies, as well as stores, websites, and suppliers.
The following are recommended steps to consider when developing an effective brand protection program.
- Early Evaluation: Before a company can take advantage of these benefits, it needs to fully understand how serious and widespread the problem of theft can be. Evaluation of the problem is the first step. Also, evaluating which anti-counterfeiting security methods work best for a company’s product and industry will allow the brand owner to get the necessary information on possible security features and packaging design that might be required as part of the final product launch.
- Risk Assessment: When identifying product risk, it is important to develop a risk inventory for the products. The level of risk associated with each product will differ depending upon a multitude of factors, including supply chain complexity, geography in which the product is sold, price points, margins, complexity to copy, and total demand expected for the product.
The next step is to assess potential brand damage. With brands among the most valuable assets a company owns, the fragile bond of trust between consumers and their products is a corporate and strategic asset that cannot be risked. Any injuries or deaths caused by counterfeits can destroy this relationship, and top management should be aware of the risk and committed to demonstrating leadership on the issue. Brand protection managers and the marketing team also should be involved and participate in assessing the risk of counterfeit attacks and the value of all proposed strategic solutions.
- Strategy Development: At this point, responses to the most pressing threats can be translated into action by organizing a method for management, information, and technology tools to respond to threats. This is also the time to allocate resources appropriately based on risk areas and draft a communications plan that covers potential causes of risk, avoidance actions, transference and mitigation actions, and potential impacts and contingency actions.
- Detection and Monitoring: To effectively protect a brand against counterfeiting, businesses must employ comprehensive detection and monitoring strategies that showcase dedication to enforcing their intellectual property rights and prosecuting violators.
This includes implementing a variety of security features on product packaging, conducting educational campaigns for public awareness, enhancing legal penalties for counterfeiting, inserting strict anti-counterfeiting terms in vendor contracts, and performing unscheduled audits on distribution partners.
Vigilance in monitoring online and physical marketplaces for unauthorized sales, fake profiles, and counterfeit listings, along with the deployment of anti-phishing software, is also crucial for the early detection of threats and swift action to mitigate brand infringement.
- Enforcement: Keeping a brand safe means making sure that rules and responsibilities related to intellectual property are properly observed, both online and in the physical world. This task often requires collaborating with the right authorities to handle issues like illicit manufacturing, copyright infringement, and counterfeit products being sold, shutting down fake websites, and taking down counterfeit listings.
- Data Analysis, Reporting and KPI Tracking: To track and measure the effectiveness of a brand protection strategy and ensure the prevention of counterfeit activity as much as possible, businesses should prioritize thorough reporting and analysis, as well as tracking key performance indicators (KPIs).
This approach enables them to assess the extent of intellectual property violations and tailor strategies to enhance security measures, moving beyond mere takedown metrics to focus on substantial reduction of infringements. By shifting the perspective from brand protection as a cost to a strategic investment, companies can not only safeguard their assets but potentially unlock new revenue streams through focused and outcome-oriented actions.
What Brand Protection Solutions Are Right for My Company?
Anti-counterfeiting features that authenticate products are both overt and covert and can be applied in numerous ways, including in product, on product in the form of labels and closure seals, on cartons where containers of products are stored, into plastic parts of individual packaging, and even onto metal and glass components of packaging.
Each feature serves a unique purpose. Covert or invisible markings enable trained inspectors to quickly authenticate genuine products in the supply chain, identify the source of diversion, or determine other illicit activities. There are also overt features that allow the end consumer to verify the authenticity of their purchased product. When combined with careful design and production quality controls in authentic product manufacturing, these features raise the bar of complexity for counterfeiters and make the product a less attractive target and far less vulnerable.
Overt Security:
Visible security features are valuable in product authentication. Visible to the naked eye or felt via touch, this category includes holograms, color-shifting inks, and security threads that are difficult to reproduce or copy. Other examples include microtext, thermographic ink, and even micro-optics (the blue lenticular strip found on the current U.S. $100 bill).
Although visible security features are a starting point, counterfeiters are creative. Even if a visible authentication feature is hard to recreate perfectly, a counterfeiter with the right tools and illegal intent only needs to copy it closely enough to confuse a consumer who just gives a package a quick glance. Additional measures create layers of security – making it more difficult, even impossible in some cases, to copy or duplicate security features.
Overt Security Tactics Include:
- Optically variable inks
- Color-shifting inks
- Pearlescent inks
- Gold and silver inks
- Thermographic ink
- Microtext
- Anti-tampering technologies (tamper-evident closures and labels)
- Optical security technologies (holographic seals and labels)
Covert Security:
High-security covert features can be embedded into labels, closure seals, or other features of product packaging. Although these covert markers are invisible to the naked eye, they can be found and measured with specialized handheld instruments using proprietary optics and detection algorithms for rapid, secure field authentication. Additional forensic layers of security can be embedded into materials and confirmed through more extensive laboratory analysis for evidence to further prosecute profiteers.
Covert Security Tactics include:
- Heat-activated inks
- Light-activated inks
- Fugitive inks
- Inks or materials with specialized fluorescing taggants
- Ultraviolet activated inks
- Machine-readable Electro ink
Semi-Covert Security:
As the name suggests, these are features that might not be noticed until someone closely examines the product or package.
- Forensic Security: Forensic analysis involves laboratory testing of products via an embedded component or molecule added to a substrate or solution to determine authenticity. Unique product elements are examined so brand owners can generate compelling evidence of counterfeiting for legal proceedings. However, the ability to trace a product back to its origin is not supported unless a unique hidden tracing element is added to the product.
Case Study: Pharmaceuticals
The Challenge:
Counterfeit copies of a major pharmaceutical brand were turning up in the U.S. market, but the brand had no security measures in place to allow patients or inspectors to tell real products from the fake. Consequently, $1 billion worth of product, already in the distribution pipeline, could not be sold until a method of allowing patients and retailers to verify that the medicine is authentic could be implemented.
The Solution:
The customer’s product was repackaged to include a variety of authentication features that could be identified by patients and inspectors, both in the field and in the laboratory. These included:
- Overt, color-shifting inks: Readily distinguishable by patients
- Covert, machine-readable inks: Detected in the field by inspection staff with appropriate readers
- Forensic markers: Only detected under laboratory analysis
The Outcome:
The Authentix solution to the customer’s counterfeiting problem provided a secure means of instantly differentiating authentic from counterfeit medicines. The benefits were immediate and significant:
- $1 billion worth of product: Frozen within the supply chain was released for sale
- The expense of a full product recall: Was averted
- The customer: Was able to mitigate the risk of potential lawsuits
- Most importantly, confidence in the brand: Was restored among physicians, pharmacists, and patients
Learn more: https://authentix.com/protecting-1-billion-pipeline-of-medicine-case-study/
- Chemical and Physical Markers: These can be hidden from consumers and counterfeiters and can only be seen with specific detectors that are calibrated to a specific wavelength to verify authenticity.
- Tamper Evident Packaging: These are labels, stickers, or seals that, when opened or tampered with, provide immediate evidence that the product has been compromised.
- Serialization: In the serialization process, a company applies individual unique codes and/or signatures at the point of manufacture (giving each product an identifiable attribute) and defines scanning locations where retrieval and association of the unit can be linked to the scanning transaction.
These transactions uniquely capture, track, and store data from those markings in a managed database that allows authorized personnel to monitor the product journey by unit or larger groups. Most are familiar with this process as it applies to shipping a package overnight where it is tracked online until it reaches its destination.
- Digital QR Codes: Products can be scanned and authenticated without the need for an app, using a smartphone camera that can then further engage consumers by directing them to other web pages where they can register their warranty, learn more about the product, and even suggest other complementary products. As the product travels through the supply chain, the unique number or symbol can be collected in the database and added to its history.
This information is available to a credentialed user via a mobile app or localized database. In a track and trace system, for instance, the information flow can be bi-directional, so the collection of the symbol, the scanning event, and the unique call to the database can be recorded and appended to the product record for verification purposes.
- Online Brand Protection: The rise in online sales has been unfortunately accompanied by the rise in counterfeiting on online marketplaces, social media platforms, and websites. As mentioned earlier in this guide, online brand protection tools include keyword monitoring, logo detection, image matching, and the use of advanced brand protection technology like Artificial Intelligence (AI) and Machine Learning. Online brand protection allows your company to easily scan web pages and marketplaces, social media platforms, e-commerce apps, messaging apps like WeChat, payment sites, and the dark web for infringing content and listings and get them taken down.
Implementing a Multilayered Approach: How Brand Protection Works
Today’s reality is that one level of security is rarely sufficient. Counterfeiting technology is constantly evolving, so a simple one-dimensional technology to combat illicit trade isn’t enough. An effective multilayered approach in which overt, covert, and forensic features are applied is the most effective long-term solution to detect and deter counterfeiting.
These features can be incorporated into labels, closure seals, storage cartons, plastic, metal, and glass packaging at very reasonable costs. Each type of feature serves a unique purpose, from color-shifting inks that allow end-users to quickly identify a branded product as genuine to covert markings that enable an inspector to identify many factors involved with the source of authenticity.
Multilayered security options Include:
- Overt
- Covert
- Forensic
- Online monitoring
- Analysis – data collection and insight
- Intellectual property and trademark enforcement
Case Study: Wine and Spirits
The Challenge:
A spirits brand based in South America needed help addressing counterfeiting and adulteration. They were losing millions in sales and experiencing a 30-40 percent counterfeit rate, which put public safety and brand reputation at risk. An authentication solution was needed to make it easier for law enforcement and health agencies to distinguish authentic from counterfeit products in the field.
The Solution:
Authentix implemented multilayered security options throughout the program, including a combination of in-product, on-package marking, and distribution channel monitoring. For authentication purposes on packaging, an overt feature was added as tamper evidence for consumers, and a covert feature was added for official retail inspectors to detect via handheld field verification readers and test kits. In addition, covert features were incorporated into the spirit itself for field and forensic lab verification.
The Outcome:
- Within the first year of the program: 75 million liters of spirits had been protected (approx. 100 million bottles)
- More than 1,300 inspectors in 28 states: Had inspected over 300 retail outlets
- Of these, 10% were found to contain counterfeits: 5 retail outlets were investigated, resulting in arrests
- The brand owner: Experienced a 25% increase in sales over the same time period
Learn more: https://authentix.com/knowledgecenter-spirits-case-study/
The Future of Brand Protection
More and more, the ubiquity of technology enables counterfeiters to produce higher-quality products that mask inauthenticity. Brand owners must begin to think differently about their supply chains and how to secure them. This means not only working with trusted partners across the supply chain but also deploying advanced tools and technologies for brand protection. Yes, it means fighting fire with fire. This is the future of brand protection.
Counterfeiters are creative, resilient, and constantly evolving. Therefore, it is important for the industry to innovate and develop new technologies. New printing techniques, for example, along with the complexity of the designs, make features more difficult for counterfeiters to replicate.
These advancements deter counterfeiting and safeguard consumer goods such as food and beverages, fashion, and even cleaning products, which are increasingly targeted by counterfeiters. In addition, developing security printing techniques and features that are economically feasible for smaller brands to adopt is essential, ensuring widespread protection across various industries.
With the increasing reliance on online platforms to sell products, brands are more vulnerable to cyber threats, hacking, and ransomware attacks. This will only increase in the years to come. And, as more people turn to social media to purchase products, companies must be ready to combat negative reviews, false information, and social media attacks. Active social media monitoring and engagement are essential for the future. Implementing strong cybersecurity measures to safeguard customer data will also be crucial.
AI, AR, and Machine Learning in Brand Protection
Two main benefits that Artificial Intelligence (AI) brings to brand protection are counterfeit detection and image and video recognition. AI algorithms can analyze vast amounts of data to identify patterns indicative of counterfeit products. This can include monitoring online marketplaces, social media, and other channels for unauthorized sellers. Advanced image and video recognition algorithms enable brands to quickly identify instances of unauthorized use of their logos, trademarks, or product images across various platforms.
Emerging technologies like augmented reality (AR) also hold immense potential to revolutionize brand protection. AR can offer an additional level of digital verification of documents or products while fostering consumer engagement and enhancing security measures.
By giving consumers the ability to scan documents or labels on products using their phone, two significant outcomes are achieved:
- Consumers can participate in interactive brand engagement activities: Fostering brand loyalty.
- Consumers inadvertently become inspectors in the field: As the absence of AR features upon scanning could indicate a counterfeit product, allowing them to instantly report it.
Benefits of Having a Brand Protection Partner
Since any trademarked product can be counterfeited, it’s imperative to have a brand protection strategy in place.
An effective brand protection program spans many company departments including marketing, legal, production, design, supply chain, logistics, and more. That’s a lot of moving parts to manage internally while companies are already busy making and selling the best products possible. The time these departments can dedicate to brand protection can be severely limited.
Having an external brand protection partner allows companies to have an entire team of experts in their corner providing custom brand protection solutions built for each company’s unique situation using the most advanced technology paired with expert analysis.
A brand protection partner will also be able to share valuable insights and analytics to make further recommendations for what next steps the company can take to combat counterfeits. Brand protection partners can work with external teams including law enforcement, border authorities, and investigators to tackle counterfeit products at the source.
What To Look for in a Brand Protection Partner
The right security technology should come from a company with sufficient industry experience, technical skills, implementation capabilities, and ongoing program management to properly support the program for multiple years.
Qualified brand protection solution providers will work with individuals, teams, and vendors to develop, implement, and manage a proactive strategy to cover all company objectives. The following factors should be considered when vetting potential partners:
Industry Knowledge and Expertise: It’s critical that the authentication partner offers consultative services, has experience with the company’s products, and understands their industry inside and out. The partner should fully understand the company’s challenges, articulate exact problems, and work to set goals for the program. In this way, a trusted relationship can be established that will provide:
- Common vision for the goals, resources, and time management of the authentication plan
- Knowledge transfer on key topics such as global regulations and advanced technologies
- A proactive approach to managing the supply chain and preventing problems
Customized Solution Offerings: Companies should select an authentication partner who can fully customize a solution to fit not only the unique challenges of their industry but also the needs of the specific organization. The partner should have the necessary expertise on what types of security features are needed for different types of product packaging, such as tamper-evident seals, foils, labels, etc. This will allow the company to take a proactive approach in combating counterfeit products. Companies need a partner who offers:
- State-of-the-art color marking systems
- Multilayered security features
- Monitoring and enforcement
- Ability to function properly in a multi-channel distribution environment
- Data capabilities including dashboards and cloud platforms
Multilayered Approach and Implementation Support: Ensure the provider offers consultative services, implementation ownership, and ongoing program support after the program is launched.
Decades of experience have proven that there is not a simple “silver bullet” technology that can be applied to all products for perfect brand protection security. As discussed earlier, a multilayered approach in which overt, covert, and forensic features are applied in various ways is the most effective long-term solution against counterfeiting.
Supply Chain Integration: More than likely, the company’s current supply chain is complicated and has many moving parts. A good authentication partner should be able to instantly integrate within that chain. In addition, the partner should be a “third-party agnostic” solution integrator without any prejudice toward other links in the supply chain. This partner will be able to objectively analyze the supply chain, identify where potential problems lie, and make recommendations on correcting them. A provider should have the following attributes:
- Third-party printer, logistic partner certification, and support
- Integration with existing systems and manufacturers
- Trial runs with actual samples for testing purposes/quality assurance
Talent and Reach: The partner should have technical and commercial teams to provide the appropriate level of experience required to authoritatively advise on the features of their technology and its implementation. In the case of a global brand, the provider should have a global footprint. This includes global reach for delivery, servicing, technical support, dealing with customs, and regulatory expertise to handle regional and country-based compliance issues.
Implementation: An experienced authentication partner should be able to certify and conduct print trials with the company’s manufacturing printers. All manufacturing of security materials should be produced in a secure facility under a full chain-of-custody protocol. A security audit is the best way to determine this.
The brand owner must be confident that appropriate physical security and auditing procedures are maintained in the potential partner’s facility. It is important to only work with a partner with quality accreditations appropriate for the subject matter and technologies involved.
Some potential partners might be great at strategy and planning and not-so-great at implementing those plans. It’s important that the partner provides extensive documentation of their experience in implementing a strategy, including a resume consisting of several multi-year customer relationships.
In addition, the partner must understand the company’s business inside and out, become an integrated part of the team, and extend that support to third-party vendors. Companies need a partner who is flexible enough to adapt to their culture, challenges, and processes. A good implementation strategy should encompass:
- Execution across the entire global supply chain
- Training and enablement for all involved parties
- Flexibility to expand and grow with changing needs
Commitment: An authentication partner must be willing to see a company through the good times and challenging times too. An ongoing relationship with the partner allows the company to stay one step ahead of counterfeit issues. An established, trusted strategy is the only way the brand protection program can sustain long-term success. It should include:
- Dedicated project manager to handle programs
- Security features testing
- Ability to retain sample programs to ensure consistency
- Ongoing reports and result interpretation that provide actionable insights
- Regular auditing of third-party vendors for proper use of security materials
In Conclusion:
Employing an effective brand protection solution brings a wide range of benefits to businesses. Improving sales and revenue is always important in any industry. By eliminating infringements and counterfeits, a company can increase revenue and market share.
Having a brand protection partner that manages detecting, monitoring, and taking down counterfeiters allows businesses save valuable time and focus on producing and selling instead of worrying about bad actors. Customers will also notice a rise in brand standards once the lower-quality infringing products are removed from the market, generating goodwill and improved brand reputation.
The elimination of low-quality, counterfeit products not only saves businesses from financial drain but also solidifies their reputation among consumers and partners alike. This newfound trust translates into lasting customer loyalty and gives businesses a competitive edge. Additionally, brand protection strategies reduce legal risks and provide actionable insights by having greater supply chain visibility and data, setting the company up for even greater success.
About Authentix Brand Protection Solutions
Authentix’s team of brand protection experts helps companies every step of the way to protect their products with the latest and greatest security technology capabilities. Here are just some of the things companies can expect when working with our brand protection specialists:
- Assessment and advisory services
- Defining the gaps between current practices and industry leading practices
- Specific recommendations for improvement
- Implementation services
- Forensic product analysis services
- Risk and vulnerability assessment
- Simulated detection by third parties
- Identification of possible materials used for security feature replication
- Prototype development services
- Product and packaging prototypes that incorporate security features designed specifically for each company
- Assistance in managing the deployment of anti-counterfeiting program technology in each facility
As the authority in authentication solutions, Authentix can help brands create a customized plan to tackle counterfeit products from every angle, collect actionable data, and protect brands and consumers. Authentix works with each company to determine which brand protection solutions are right for their situation.
Authentix brings enhanced visibility and traceability to today’s complex global supply chains. For over 25 years, Authentix has provided clients with physical and software-enabled solutions to detect, mitigate, and prevent counterfeiting and other illicit trading activity for currency, excise taxable goods, and branded consumer products.
Through a proven partnership model and sector expertise, clients experience custom solution design, rapid implementation, consumer engagement, and complete program management to ensure product safety, revenue protection, and consumer trust for the best known global brands on the market. Headquartered in Addison, Texas USA, Authentix, Inc. has offices in North America, Europe, the Middle East, Asia, and Africa serving clients worldwide.
Download the Complete Brand Protection Guide
Complete this form for access to the pdf version of the guide.

Thanks for your submission!
